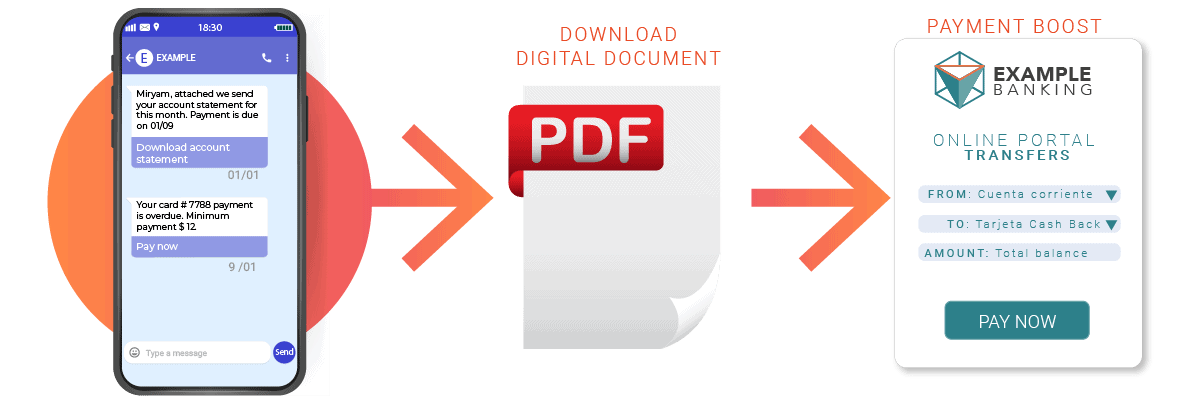
Excellent Reasons On Deciding On Credit Card Apps
Wiki Article
What Constitutes A "Suspicious" Act And Can Result In A Credit-Card Being Blacklisted?
Certain actions or behavior could be suspect and result in a credit card to be blocked or flagged. Some examples of suspicious behaviors include: Unusual Spending patterns
Sudden large transactions or an increase in spending compared to the usual behavior of the cardholder can trigger suspicion.
Unrecognized Transactions -
Fraud can be detected by any unauthorized or unfamiliar transactions that are reflected on the statement. The cardholder didn't authorize or initiate.
Multiple Refused Transactions
A pattern of several failed or declined transactions in a short time period, particularly if the cardholder has a generally good transaction history could indicate an issue.
Geographic Anomalies
Transactions from locations significantly distant from the typical spending area or multiple transactions from various geographical locations within a brief period of time may raise suspicion.
Purchase types that aren't normal
It is possible to flag suspicious purchases. These include purchases with high value which aren't in line to the typical spending patterns.
Uncommon Online Behavior
Unexpected online activity, such as numerous failed login attempts, altering account details or suspicious login attempts may indicate an unauthorized access.
Unusual Card Use
When a card's normal usage pattern is disturbed, it could be considered suspicious. For example, if a local credit card suddenly is used for international transactions.
Sudden Cash Advances or Transfers-
Cardholders might receive notifications for advances or cash transfers that are outside of their normal spending practices.
Frequent Transactions that are not present on the card
It is possible to flag a sudden increase of card-not-present transactions (online purchases or phone-based transactions) without a previous record.
Problems with Identity Verification
The difficulty of verifying a cardholder's identity during transactions, particularly in situations when additional verification is required, could lead to suspicion.
The card issuer might investigate any of these behaviors or monitor them, and then temporarily stop your card until you are able to verify that the cardholder is in fact who they claim to be.

What Should I Do When I Suspect That My Credit Card Is Blacklisted?
If you suspect that your card may be listed as blacklisted, or if you suspect there was fraudulent activity linked to your card, immediately notify your card issuer.
You can dial the number for customer service on the card's back or go to the issuer's website to check if they have an anonymous hotline for reporting fraud.
Inform the issuer of any concerns you be experiencing, like a suspicion that fraudulent activity has taken place or your card has been compromised.
Report Suspicious Activity-
Report any unusual or unauthorized transactions on your account.
Please provide detailed information regarding the transaction that you are concerned about. Please include dates, figures and, if possible merchant names.
Request Card Blocking or Replacement-
To avoid any further unauthorized transactions To prevent future unauthorized transactions, request that your credit card company temporarily block the card.
Find out about the replacement procedure of the card with credit access.
Check your account and contest charges
Check your statements on your account to look for any suspicious transactions you may have overlooked.
You can report unauthorized transactions to the credit card company to ensure that the transaction is investigated and resolved.
Make sure you keep track of your credit score.
Follow up with the credit card company to confirm that the appropriate actions have been taken to address your concerns.
Monitor your account to see whether there have been any unusual changes or suspicious activity.
You might want to consider putting up a fraud alert or a security freeze
You may want to add the security freeze on your credit report, based on how serious the issue is. This will help to stop fraudulent activity or identity theft.
Report to Authorities if Necessary-
If you suspect that identity theft or fraudulent activity is taking place, you should report the situation to the Federal Trade Commission and file an official police report in your area.
It is essential to take action promptly to stop any more fraudulent transactions from happening and minimize the potential loss. You can limit the effects of fraud on your credit card and abuse by reporting suspicious activities promptly to your credit card company.
Cybersecurity Experts Are Trained To Identify And Monitor Cyber Threats Including Credit Card Details.
Cybersecurity experts monitor and identify threats such as compromised credit card numbers with a variety of techniques and tools. The most popular methods and practices are: Threat Intelligence Gathering
To stay up to date on security threats and vulnerabilities, it's essential to gather information from various sources. These include forums and threat feeds and tools for monitoring the dark web, and security advisory services.
Network Monitoring and Intrusion Detection
Monitoring network traffic using specialized software and tools, looking for anomalies or suspicious behavior that could indicate an unauthorized data breach or access.
Assessment of vulnerability and Penetration TestingAssessment of vulnerability and Penetration Testing
Conducting periodic assessments to discover weaknesses in systems, applications or networks. Testing penetration tests involves performing the use of simulated attacks to reveal vulnerabilities and assess the organization's security capabilities.
Security Information and Event Management Systems (SIEMs)
Implementing SIEMs that analyze and aggregate log information (from firewalls as well as applications and servers) in order to recognize, track, and react immediately to security breaches.
Behavioral Analysis
Using behavioral analyses to detect patterns that are unusual or different from the normal behaviour of users within a system or network, that could indicate a possible breach.
Threat HuntingThreat Hunting
Searching for threats or suspicious activity within an organization’s network by analyzing logs, traffic and system data. This can help uncover security threats that aren't detected by traditional security methods.
Endpoint Security Solutions
Protection of systems and devices from malicious activities by using endpoint security solutions, such as antivirus, antimalware and even endpoint detection and response (EDR) tools.
Data Protection and encryption
Implementing encryption techniques to protect sensitive information like credit cards as it is transferred and stored it will lower the likelihood that data breaches will occur.
Response to an incident and Forensics
Implementing a plan for incident response can allow you to swiftly respond to any incidents. Conducting forensic analyses to identify and understand the scope, impact, and source of security breach.
Security professionals from Cybersecurity combine these methods together with a thorough knowledge of cyber-related threats and compliance requirements, as well as the best practices to recognize and combat cyber-attacks. This includes those involving stolen card data. A proactive security approach, continuous monitoring and intelligence on threats are vital to maintaining a robust cyber security. View the recommended savastan0 for blog advice.